External access of SharePoint Online content has come a long way since my previous article about a similar topic. After some initial bumps like the requirement of having to register external accounts as microsoft accounts (remember gmail ID registered as microsoft ID, still confusing right?), Microsoft seems to have got it right this time.
In combination with “SharePoint and OneDrive integration with Azure AD B2B“, google federation makes external sharing of SharePoint Online and OneDrive content/sites a piece of cake. This could really help organizations push through the external sharing feature to business users, who have been a bit reluctant in adopting OneDrive content Sharing due to complex sharing invitation redemption experience.
What does Google Federation mean?
For the newbees in SharePoint Online world, this simply means that external users will be able to access the shared content with them using their existing gmail ID and password. So, you share any document/folder/site with any external user’s gmail ID and they can just login with their own gmail password. No multiple steps invitation redemption, no remembering different passwords. If the user, with whom the content has been shared, is already logged into any google service, like gmail, he/she won’t even need to enter any password! Neat, isn’t it?
This configuration is valid for all other Office 365 Services as well which uses Azure B2B based external access like OneDrive, MS Teams, Planner etc.
How to go about that?
Setting up Google federation in your Office 365 tenant, even though includes a few steps, is fairly straightforward. Let’s take a look at the steps involved.
Create a new Shared Gmail Account
First thing first, create a new Gmail Account. Well, even though you can use your personal gmail account for this configuration, it is wise to create a new one which can be shared with other team members for future maintenance. If you are just doing a POC in a dev/test tenant, you can skip this step and just use your personal gmail account. It’s super easy to remove the federation afterall.
Create a Project in Google Developer Console
Go to https://console.developers.google.com and login with your newly created gmail account and create a new project.
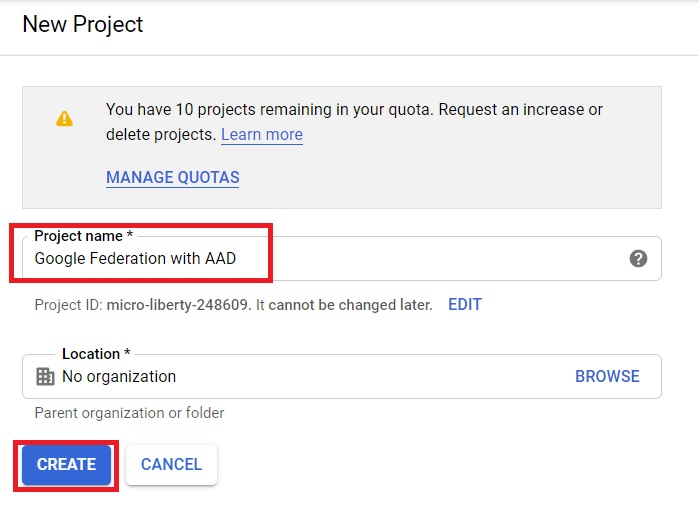
Configure OAuth Authentication
Once the project gets created, we need configure OAuth2 Authentication. Ensure that project is the selected one on the screen and click on “OAuth consent screen” tab on the left. On the next screen select “External” and click Create.
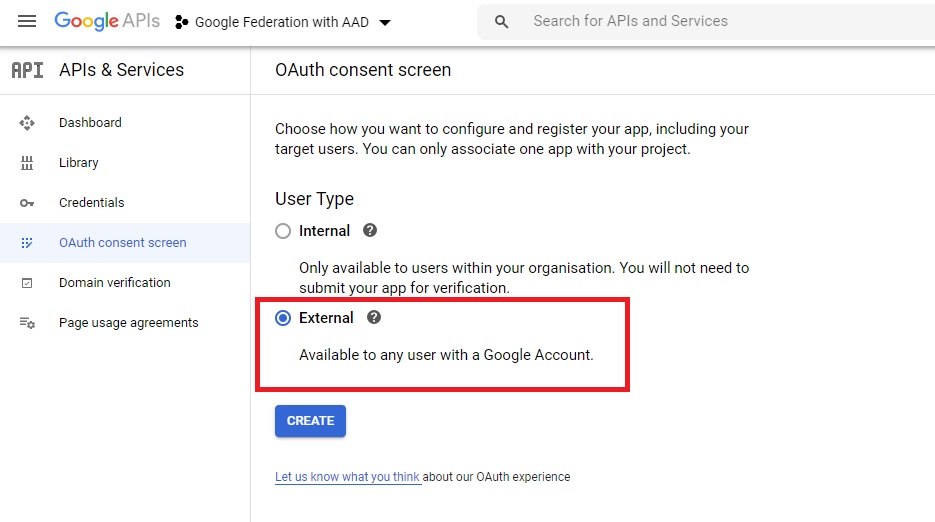
You will be redirected to App Creation screen. Fill in the App Name and a support email
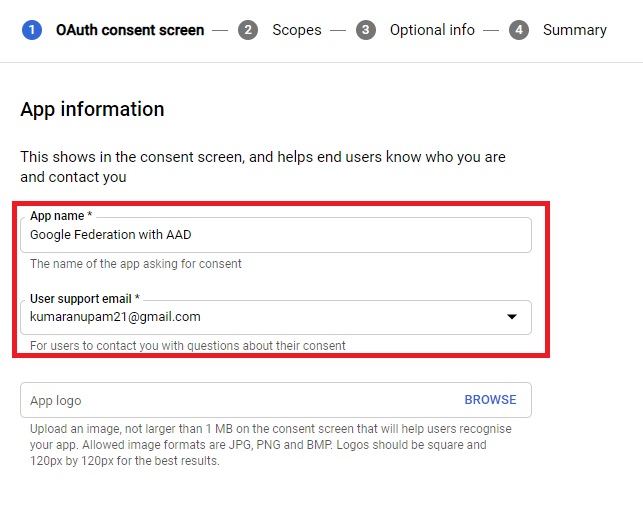
Scroll down the screen and find the field “Authorized domains”. Click on Add Domain and Type in “microsoftonline.com” in the field. Type in a developer contact email and press Save and Continue.
On the next screen, Click on Add Or Remove scopes
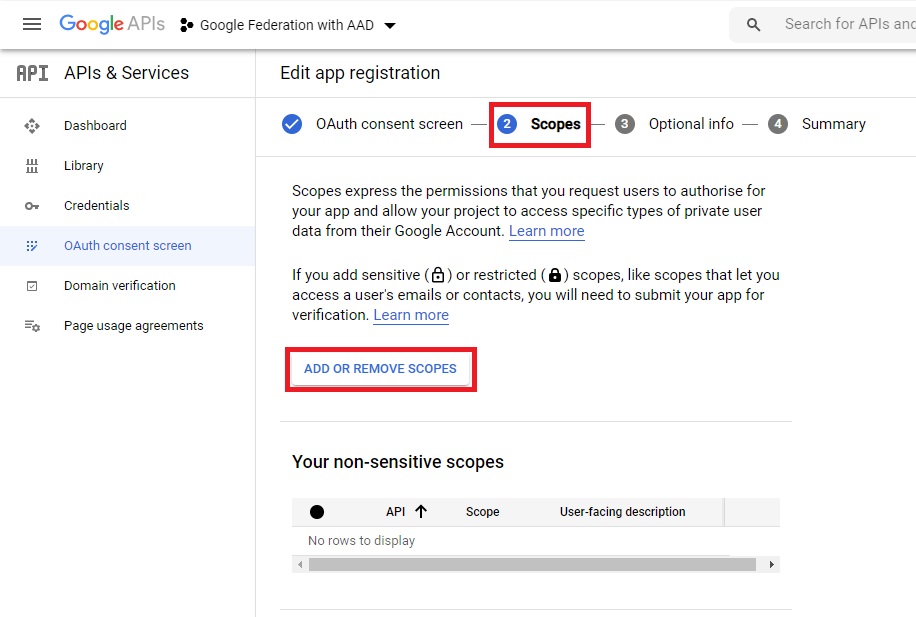
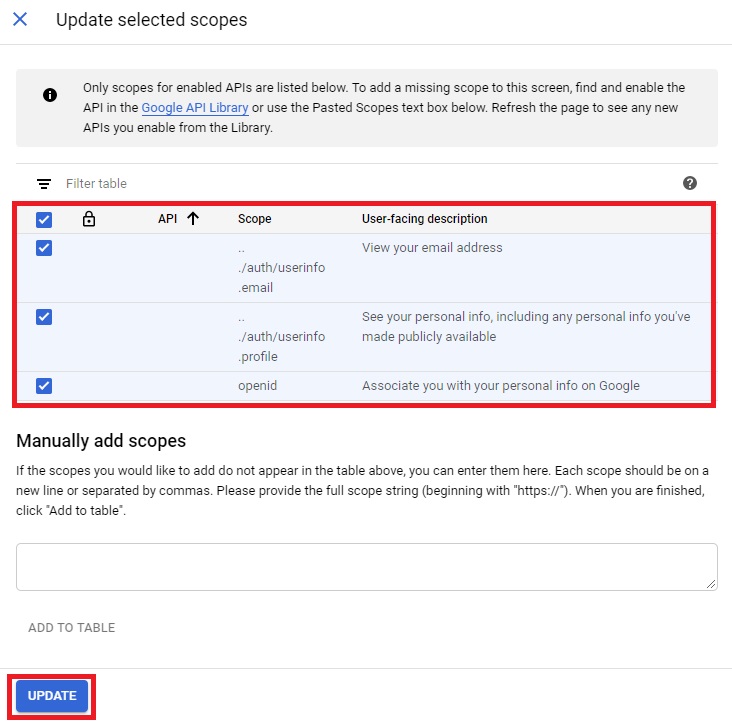
And select all the scopes listed. These scopes are non-sensitive
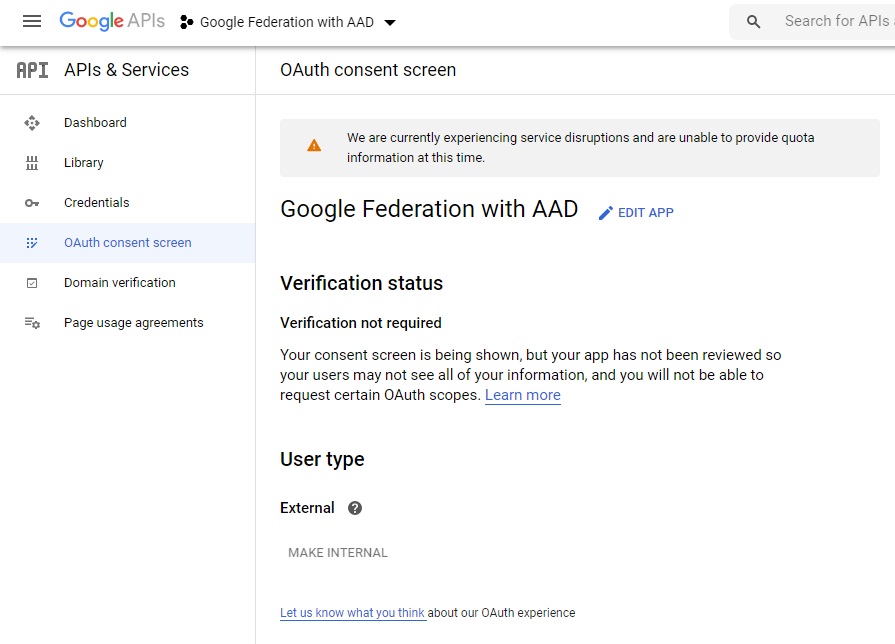
At this point, the app has been created and your OAuth Consent Screen landing page would look something like this
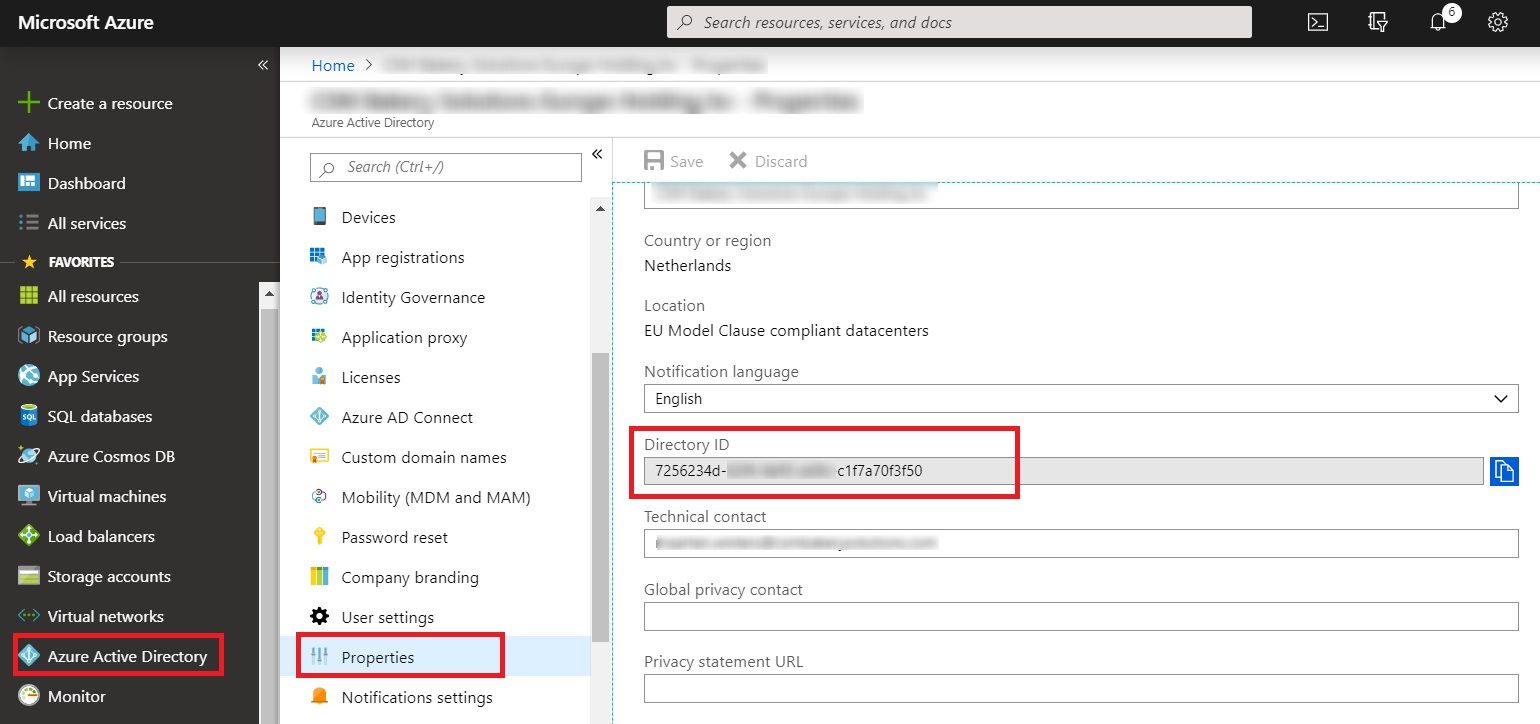
Find Directory ID
Before we continue with the remaining configuration of the newly created google project, we need to find out the Directory or popularly called Tenant ID of the Office 365 tenant.
Go to Office 365 Admin portal and select Azure Active Directory from under Admin Centers. On the target page, select Azure Active Directory again from left navigation and select properties. You will see the Directory ID under Directory ID field in right side of the screen. Note down the ID, we’ll need this in next configuration.
Generate OAuth Credentials
We are almost there. Click on the first tab “Credentials” and the under “Create Credentials”, select the option “OAuth Client ID”
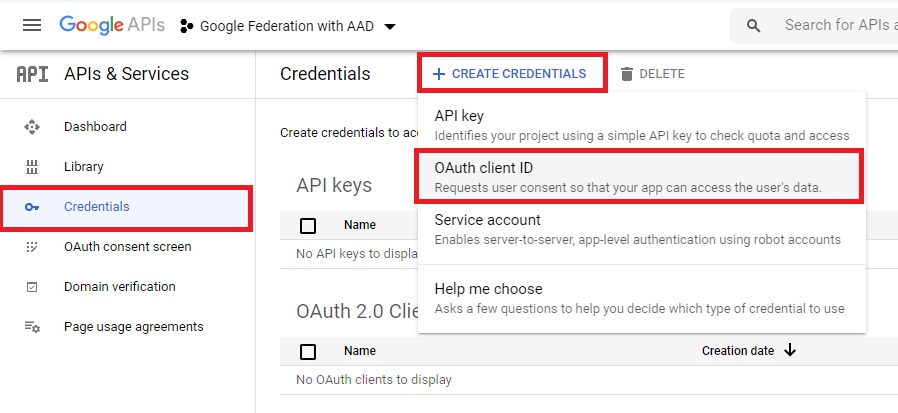
Now we need to create an OAuth Client ID
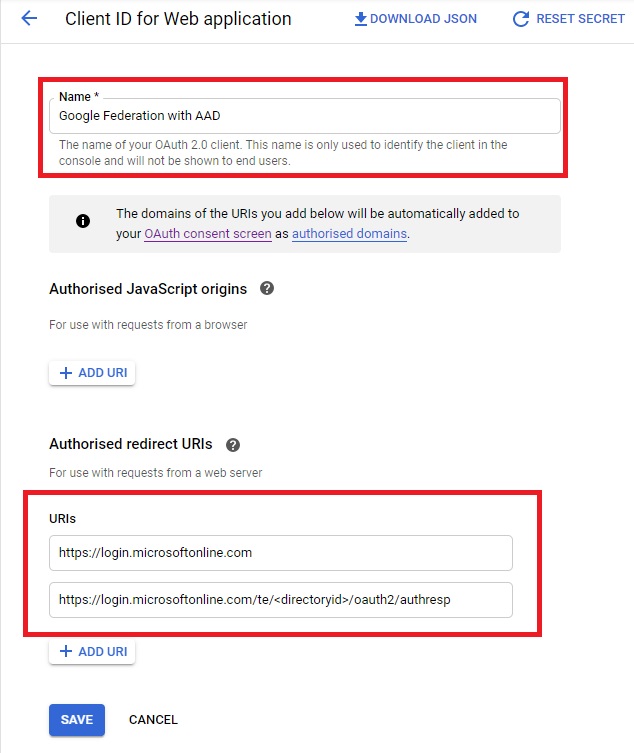
Select “Web Application” under Application type and provide a name to the application. Scroll down the page and find the Authorized redirect URIs section. Add the following URIs in the field.
- https://login.microsoftonline.com
- https://login.microsoftonline.com/te/<directory id>/oauth2/authresp
Replace the <Directory ID> with the ID noted in the previous step and click on Create.
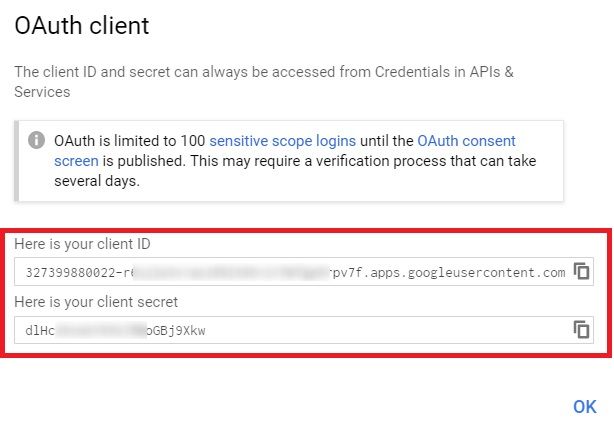
If everything went well, you would see a popup screen showing the ClientID and Client Secret. Note them down somewhere safe.
Now we are done with Google side of configurations. Let’s go back to our Azure AD and complete the Federation settings.
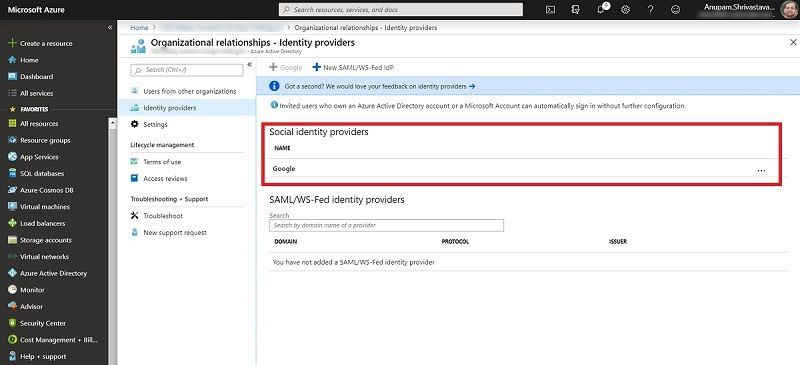
Configure Google Federation in Azure AD
Login to Azure AD and go to Organizational Relationship and click on Identity Providers. Click on Google on top and enter the Client ID and Client Secret copied from Google App and click Save.
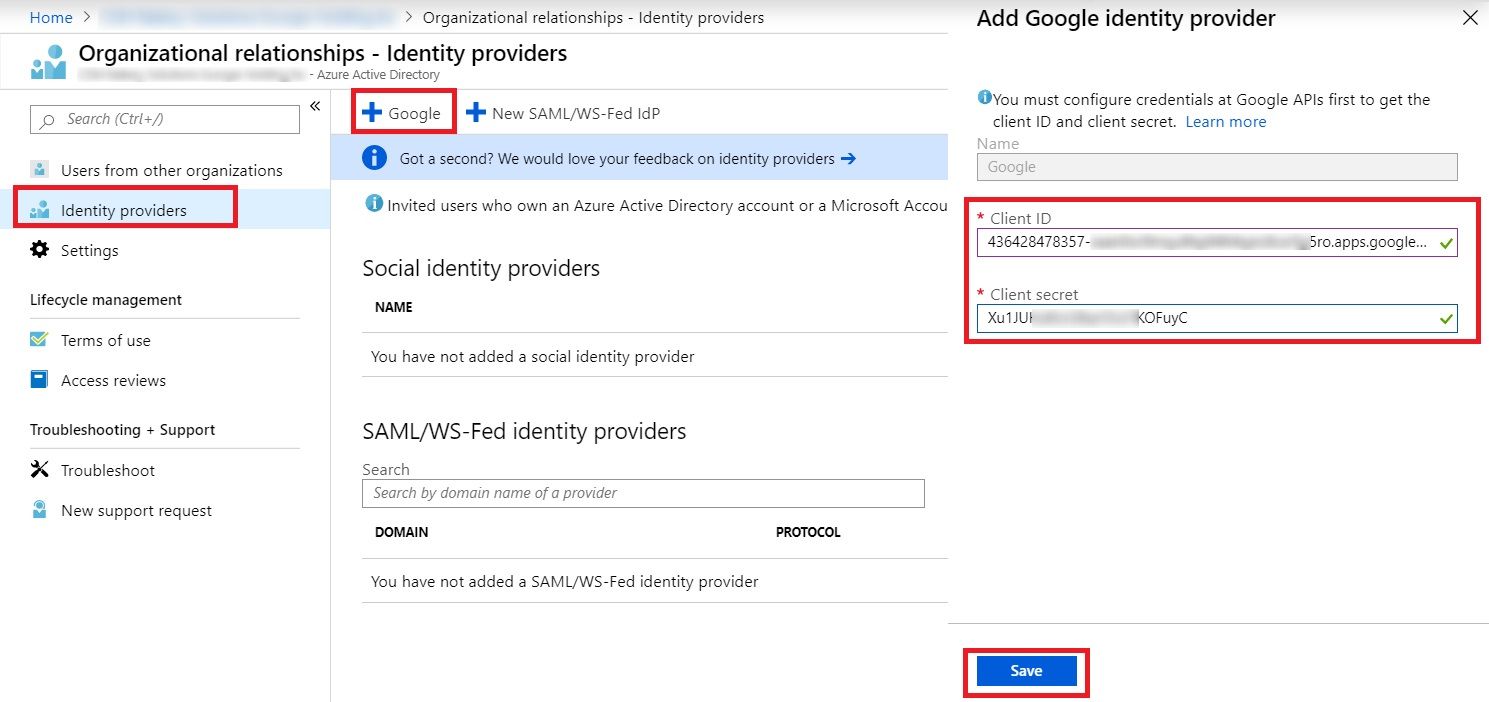
And all configuration Done! You can now see, Google listed under “Identity Providers”. If you want to remove the federation after your POC, just click on Delete from the context menu.
Content Sharing from SharePoint
So, what changed for users who want to share the content with externals with Gmail ID. Well practically nothing!
You still go to SharePoint site/folder/document and click share and type in the gmail ID of the external user.
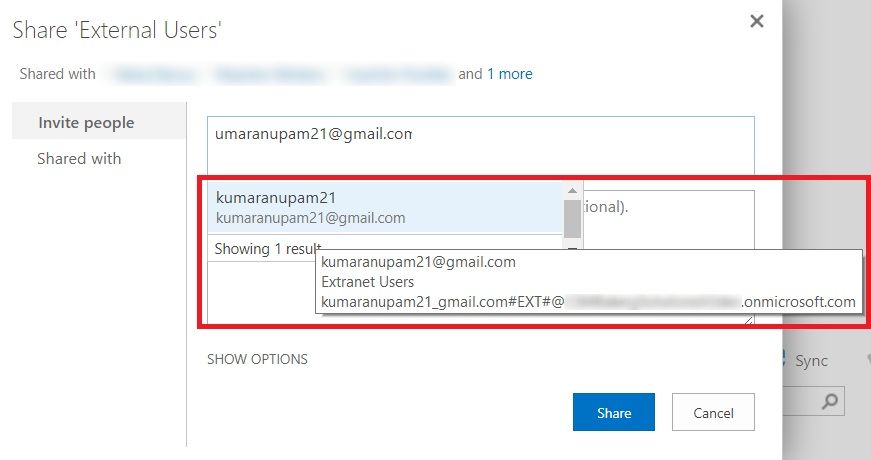
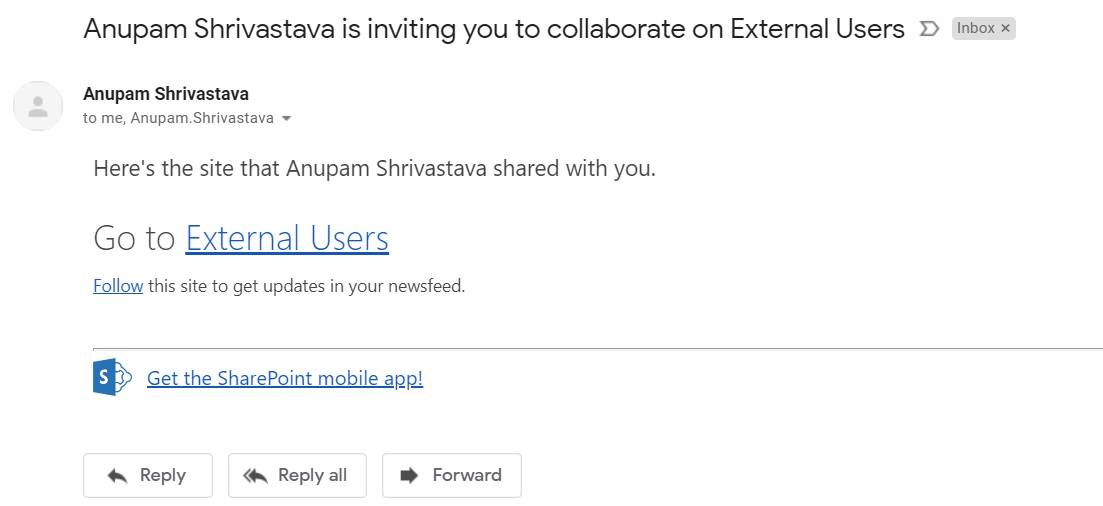
Invitation Redemption Experience
This makes this feature really awesome. And how does it look like. Let’s see… the invited user receives the invitation in their gmail ID.
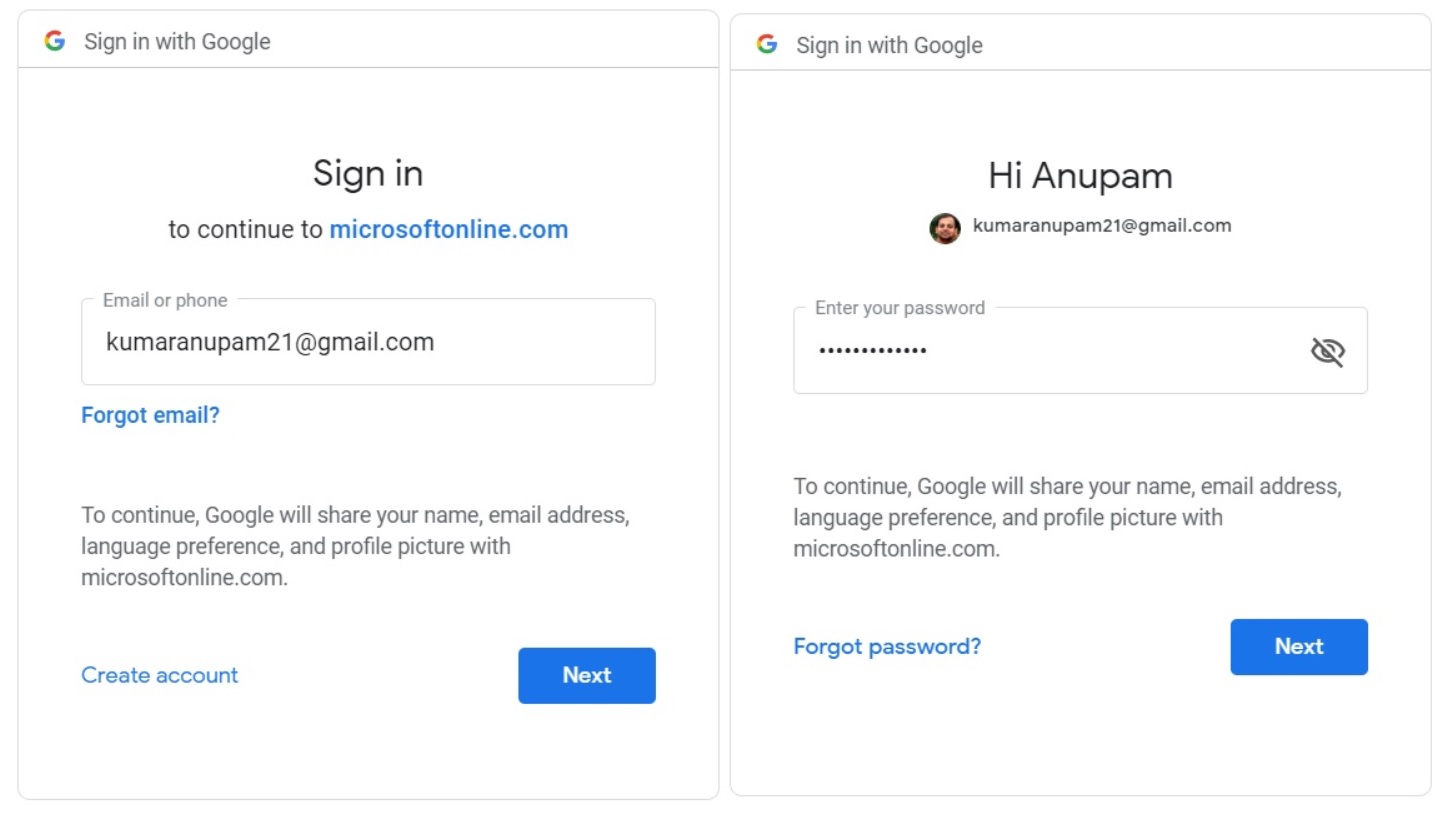
And all they have to do is to click on the link. They will be redirected to google login page, if not already logged in. All they need to do is ti provide their gmail credentials.
If this is the first time, a SharePoint content has been shared with them, they will need review the permissions to provide confirmation on a consent window.
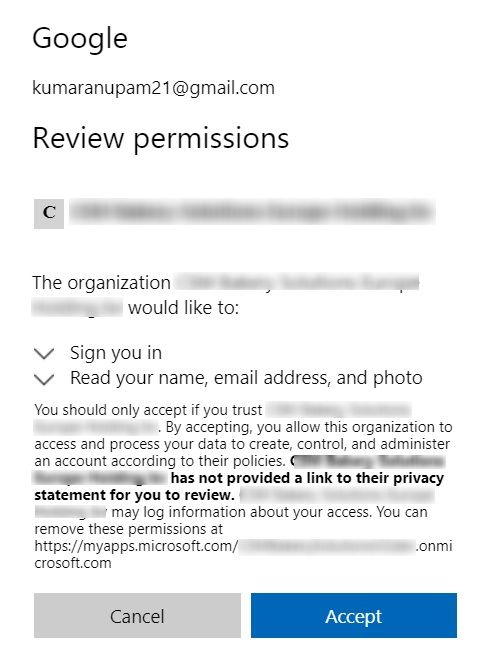
And that’s it. They would be redirected to the content shared with them immediately after that with their Gmail account.
Hope this helps.
Enjoy,
Anupam
11 comments
Can’t get this to work at all.
The users never get the google logon prompt when clicking on the sharepoint online link, Chrome says the site is not trusted.
Any ideas
Thanks for this. It’s helpful to know that this technology is available to us.
Anupam, thanks for sharing this excellent article. Congratulations ..! 🙂
What should be done so that two organizations that have different SharePoint tenant can have access to the content of the sites of one or the other tenant with the credentials of your organization?
Hi Xander, this is fairly easy. You can just enable External sharing in both tenants and add users from each others tenants as guests in each others sites. This article, a bit outdated now though, provides some details about the same.
I work in a not for profit organisation covering 99 countries that has a shared global o365 tenant and we have implemented global intranet based on SharePoint online. However, only the countries that are part of the global tenant can access the SharePoint site. Some countries in the organisation have their own separate o365 tenant, others are still on-prem, and one is on Gsuite. We have figured out how to enable collaboration and read-only access to the SharePoint global intranet site through external sharing by enabling guest user access using Azure B2B AD and MFA. However, with our GSuite countrty it looks like a direct federation between G Suite and the global Office 365 tenant would place that countrie’s accounts directly in the global tenant. These accounts would not be able to consume guest licenses attached to the p1, p2 licences and would instead require directly applied Office 365 licenses. Is this correct and, if so, how would we manage this?
No Zina, as far as I know, when you federate with Google accounts, it just takes care of Authentication – So, instead of code received over email, they can use their Google credentials. Those federated users will still be treated as Guest users and not like regular users. So those Google users will NOT require any license to access your tenant’s content.
But this article is specifically about GMAIL users and NOT if you have users in G Suite. You can take a look at https://docs.microsoft.com/en-us/azure/active-directory/b2b/direct-federation for that. Those users will still be treated as Guest users and won’t require any licenses.
Thank you so much, Anupam for your prompt response, extremely helpful
Hello,
Just followed the steps but with no luck. Users are not searchable in Azure AD and when I share a site or document in SharePoint Online, the acess flow user experience shows the same screen as before (Microsoft or Work or School Account).
Can this take a few days to be working?
Thanks
Miguel
I can’t imagine why it would take days!
Try these:
Experiencing same issue as Miguel Isidoro. As suggested tried to use an incognito window (negative) and using the gmailID at the Microsoft account login window (negative).
I tried again in one of the tenants where I had configured this. Got the MS login screen first and then I typed in my gmail ID and it redirected me to the Gmail Login screen.
I will cross check the article, if any of the configurations have been changed by MS in the meantime.