I wrote an article about Guest access in MS Teams more than a year ago which explains the Invitation flow for enabling Guest access. Even though some of the steps and screenshots are not up-to date in that article anymore, one thing which hasn’t changed since then is that Guest access is still a tenant level setting (till the time of writing this article). So, you can either enable Guest access for all your current and future Teams or disable it for all.
What are we looking for?
In SharePoint, you can enable Guest access at tenant level and then control it at each site collection level whether you want that to be enabled/disabled in individual site collections. But with Teams gradually getting more prominence and organizations trying to move to teams, lack of this feature comes as a roadblock. Wouldn’t that be nice to be able to control guest access in teams in a similar way as it’s done in SharePoint – at Individual team level?
What are the Alternatives?
As you already know Teams is based on Office 365 Groups, so one easy way seems like just to the Office 365 group from SharePoint and disable external access from there.
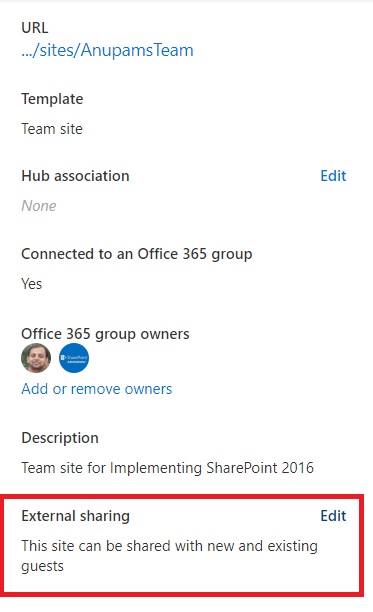
Well this will get you halfway. After disabling guest access this way, you would see that as a team owner, you can still add new guests to your team. Then what changed? The access to “Files” tab. When your guests visit the team and click on Files, they will be greeted with a nice “Access Denied” message.
However, they can still do all other activities like Chat, Calls use other allowed app etc. So, that’s not very useful, is it? Well, only in cases when you want to block File sharing access to guests, then that’s the way to go.
Solution
Keeping it short, let’s just jump into the solution right away. Even though at the time of writing this article, there is no UI in MS teams to disable guest access at individual team level, that can be done using PowerShell. What we need to do is to delve into “Azure Active Directory cmdlets for configuring group settings”.
Enable Guest Access at Tenant Level
But before we do that, Guest access needs to be enabled at tenant level in Teams. Just to to Teams Admin Center >> Org-wide settings >> Guest access and switch on “Allow guest access in Teams”.
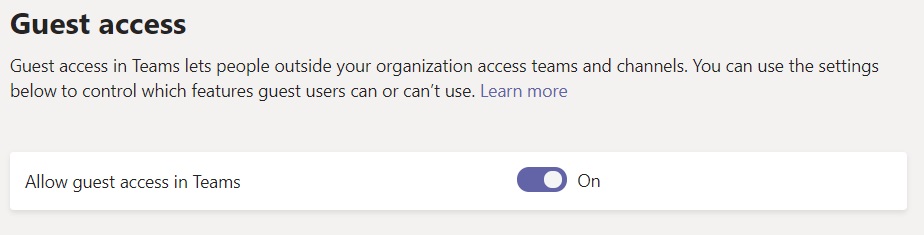
If Guest Access in off at tenant level, any changes at individual team level will not be used and it will remain disabled for all teams.
Disable Guest Access in All Individual Teams
Once the Guest Access is enabled at the Tenant level, any new Team that gets created, inherits that setting by default. So essentially, Guest Access gets enabled in all teams. So, first step is to switch it off in all teams and then in next section we’ll see how to enable it again in selected team(s).
#Ensure that latest version of AzureAD and Teams modules are installed
Uninstall-Module AzureADPreview
Install-Module AzureADPreview
Install-Module MicrosoftTeams
#Admin user credentials
$Username = "<admin user>@tenant.onmicrosoft.com"
$passwd = ConvertTo-SecureString "password" -AsPlainText -Force
$cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $Username,$passwd
#Connecting to AAD
Connect-AzureAD -Credential $cred
#Connecting to MS Teams
Connect-MicrosoftTeams -Credential $cred
#Connecting to Exchange Online
$Session = new-pssession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -credential $cred -Authentication Basic -AllowRedirection
Import-PSSession $Session -AllowClobber
#Getting all the O365 Groups
$0365Groups = Get-UnifiedGroup -ResultSize Unlimited
foreach($0365Group in $0365Groups)
{
try
{
#Check if the Channel exists. This line will throw an exception if the group is not associated with a team.
#This is to ensure that we are disabling external access only for those groups which have teams associated.
$teamChannel = Get-TeamChannel -GroupId $0365Group.ExternalDirectoryObjectId
#Check if the property exists
$GroupSettings = Get-AzureADObjectSetting -TargetType Groups -TargetObjectId $0365Group.ExternalDirectoryObjectId
if($GroupSettings)
{
$GroupSettings["AllowToAddGuests"] = $FALSE
#Updating the Property to restrict adding Guest User
Set-AzureADObjectSetting -Id $GroupSettings.Id -DirectorySetting $GroupSettings -TargetObjectId $0365Group.ExternalDirectoryObjectId -TargetType Groups
Write-Host "Updated for " $0365Group.DisplayName -ForegroundColor Green
}
else
{
$template = Get-AzureADDirectorySettingTemplate | ? {$_.displayname -eq "group.unified.guest"}
$settingsCopy = $template.CreateDirectorySetting()
$settingsCopy["AllowToAddGuests"]=$FALSE
#Creating the Property and setting the value to restrict adding Guest User
New-AzureADObjectSetting -TargetType Groups -TargetObjectId $0365Group.ExternalDirectoryObjectId -DirectorySetting $settingsCopy
Write-Host "Updated for " $0365Group.DisplayName -ForegroundColor Green
}
}
catch
{
Write-Host ($0365Group.DisplayName + " is not a Team")
}
}
What the script above essentially does is that it removes the feature of guest user addition in all teams by owners, as if it’s disabled at tenant level.
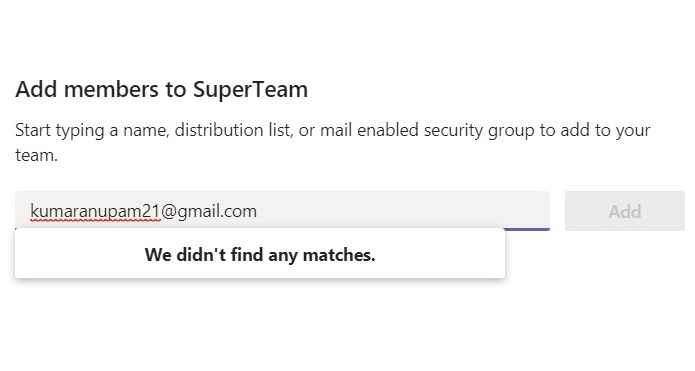
You can verify the result by going into any existing Team and trying to add any guest as member. All teams would now that “We didn’t find any matches”.
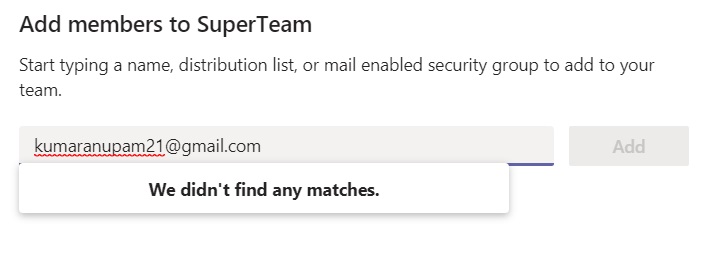
After the above script is executed, no new Guest can be added in any Teams, but already added Guests will continue to have access of teams where they are member of.
Enable Guest Access in Selected Teams
The above script is kind of self explanatory. We are looping through all the teams (actually groups) and disabling the ability to add guest users by setting a property called “AllowToAddGuests” to False.
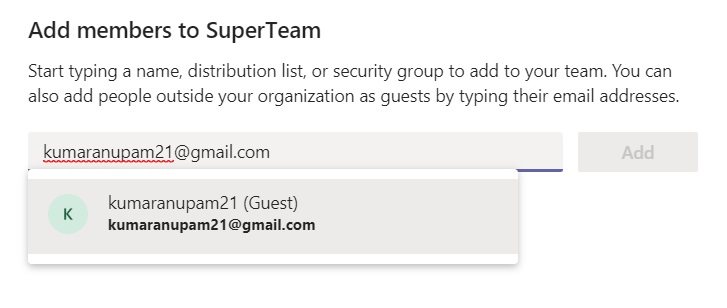
So, all we need to do is to set this property to true for the selected team(s). The script below, looks for a team called “SuperTeam” in your tenant and enables Guest access.
#Admin user credentials
$Username = "<admin user>@tenant.onmicrosoft.com"
$passwd = ConvertTo-SecureString "password" -AsPlainText -Force
$cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $Username,$passwd
#Connecting to AAD
Connect-AzureAD -Credential $cred
#Connecting to Exchange Online
$Session = new-pssession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -credential $cred -Authentication Basic -AllowRedirection
Import-PSSession $Session -AllowClobber
#Getting the selected MS team named "SuperTeam"
$0365Group = (Get-UnifiedGroup -Identity "SuperTeam" -IncludeAllProperties)
#Check if the property exists
$GroupSettings = Get-AzureADObjectSetting -TargetType Groups -TargetObjectId $0365Group.ExternalDirectoryObjectId
if($GroupSettings)
{
$GroupSettings["AllowToAddGuests"] = $TRUE
#Updating the Property to restrict adding Guest User
Set-AzureADObjectSetting -Id $GroupSettings.Id -DirectorySetting $GroupSettings -TargetObjectId $0365Group.ExternalDirectoryObjectId -TargetType Groups
Write-Host "Updated for " $0365Group.DisplayName -ForegroundColor Green
}
else
{
$template = Get-AzureADDirectorySettingTemplate | ? {$_.displayname -eq "group.unified.guest"}
$settingsCopy = $template.CreateDirectorySetting()
$settingsCopy["AllowToAddGuests"]=$TRUE
#Creating the Property and setting the value to restrict adding Guest User
New-AzureADObjectSetting -TargetType Groups -TargetObjectId $0365Group.ExternalDirectoryObjectId -DirectorySetting $settingsCopy
Write-Host "Updated for " $0365Group.DisplayName -ForegroundColor Green
}
Once enabled, you can see, the add members starts to resolve all guest users for that particular team only.
Conclusion
You may think, it as a long article for almost small one-liner PowerShell solution. But , I feel more relevant question is how to put this solution in practice so that allowing Guest access can follow some governance.
How I would go about this is to either put a process or automation around Teams creation in which by default all teams get created with Guest access as switched off unless the requestor provides a valid justification for it to be enabled in their team.
Hope this helps.
Enjoy,
Anupam
9 comments
Thank you very much for these scripts, one question, if I run this script in my O365 tenant it does Not identify any Office 365 Group as being “Teams” enabled? Any idea why the script does not identify any Office 365 Groups as Team in my tenant? (If I review the output of the script to set the AllowToAddGuest to False I do not find a single Teams Group that this value could be set for it just states “is not a Team”?)
You mean, you know that some of those groups are actually connected with Teams and still the line below doesn’t return any channel?
$teamChannel = Get-TeamChannel -GroupId $0365Group.ExternalDirectoryObjectId
Try running thie commands before you run the script:
Uninstall-Module AzureAD
Hi Anupam, thank you for the feedback, yes that is correct, I have also raised this with Microsoft, currently awaiting feedback, we have approx. 8000 teams in our tenant and when I run this script not a single Team is identified as a Team, can it possible be a configuration issue on our side?
Hi Werner,
I just verified the script again in one of my test tenants and it’s working as expected. One of the reasons I can think of is that the script is throwing exception on some other like and goes to catch block. Since the logic to show xxx is not a team is being shown under catch block, it shows all your team as not a team.
What I would suggest is to just debug the script or put an if condition under foreach loop like if ($0365Group.DisplayName -eq “your teams display name”) and see which line is throwing the exception. It could be a permission issue in Azure AD (AAD), as the script tries to create a property in AAD.
Try with an account which has admin permission in AAD as well.
Thanks for the nice summary about this. I am a tech and new to Teams. Just helping a small client get it setup for their business. I couldn’t believe you can’t just choose which Teams to allow guest access for. Also, if it were up to me the Teams Guest access options would have the option settings for all the other pieces like sharepoint, groups etc. So you can set the guest access settings for each Team all in one place (Everything right there on the Team admin page)
Nice Summary Anupam.
Teams allows any new guest to be added as guest once tenant Guest Access is “ON”.
How can we limit Teams Guest Access to ‘Existing Guests’ only? Any new guest addition would follow B2B process. Any Idea?
SharePoint/OneDrive external sharing can be set to “Existing Guests only”. We don’t see similar settings for Teams.
I added a filter to the Get-UnifiedGroups cmdlet:
$0365Groups = Get-UnifiedGroup -ResultSize Unlimited -Filter {ResourceProvisioningOptions -eq “Team”}
This will only return 365 groups that have an associated Team so that any other 365 groups are left alone.
Yes correct, but be aware that the ResourceProvisioningOptions property might not contain “Team” for some old or inactive teams. This is a known issue with the Graph.