Sometime ago, I wrote an article about how to achieve http to https redirection in Azure hosted VMs. That solution is still applicable if your Azure environment was built using Classic model and is using Cloud Services.
Things are a bit different in Azure Resource Manager model and that’s for good, as it has become even easier to achieve the same.
Problem Statement
Let’s take a relook at what we are trying to solve here.
- You have web application (let’s say SharePoint, but this solution is valid for any other web application as well) hosted in Azure VMs, build using Azure Resource Manager (ARM).
- Azure Load Balancers are used to route the incoming users’ requests to the VMs hosting your application.
- You have users accessing your web application from within the company network as well as Internet.
- Everyone should access the sites over HTTPS only, including from within office network to avoid any security issues, since content is now hosted outside organization’s firewall in an external data center.
- You want the HTTP to HTTPS redirection working. Means, if any user tries to access your web site over http, it will automatically get redirected to https.
Initial Thoughts
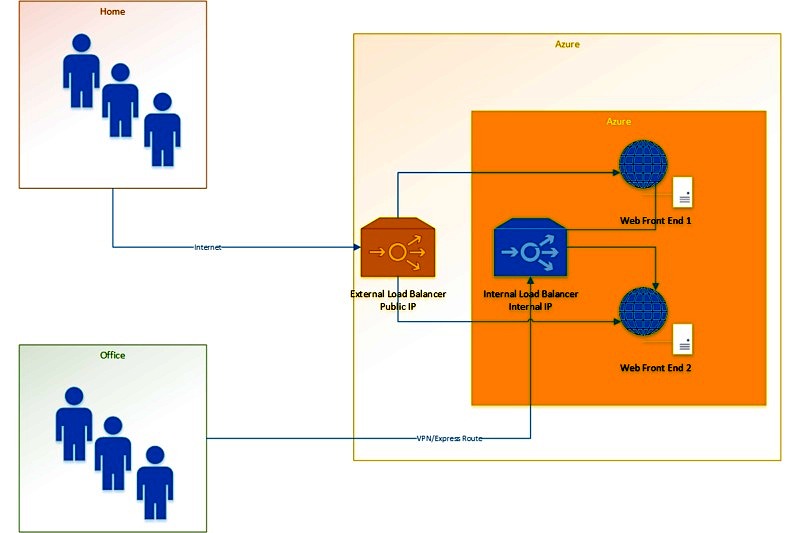
So, how to achieve this? I guess the initial thoughts would be to just add 2 load balancers in Azure
- One External Load Balancer with Public IP – for users coming over internet
- Rule 1: port:80, backend port: 443 – so that all http requests get redirected to https
- Rule 2: port 443, backend port: 443 – so that all https requests remain on https
- One Internal Load Balancer with Internal IP – – for users coming over company network
- Rule 1: port:80, backend port: 443
- Rule 2: port 443, backend port: 443
Smart, right… seems like not so, as
- You can’t add same backend port in 2 rules
- You can’t add same backend port even in 2 different load balancers!
If you try to configure like this, Azure portal will throw an error and these configurations won’t get saved.
So, we need to look for some workaround, right.
Solution
Step 1:
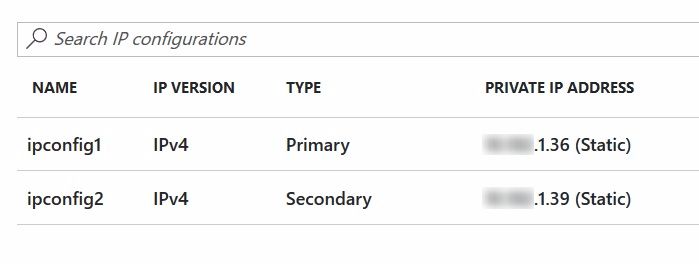
- In all of Web Front End VMs, add another static IP in the same NIC. I will not go into the details about how to do so, but that can be done from Azure Portal –> your VM –> Network Interface –> IP Configuration –> Add
- One done, all your web front end VMs would have 2 IPs assigned, Let’s say VM1-IP1, VM1-IP2, VM2-IP1 & VM2-IP2
Step 2:
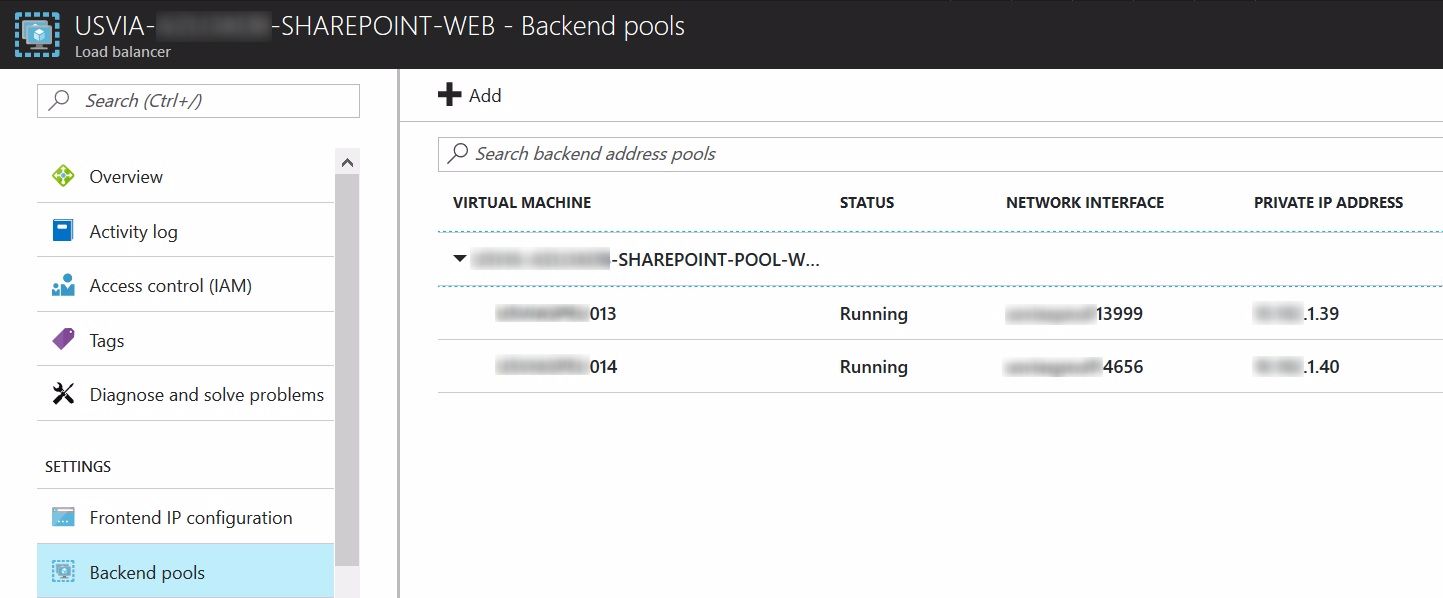
- Next step is to associate these IPs with the two load balancers
- Go to your external load balancer first and under backend pool, add the VMs with IP1
- So, your backend pool should show both front end servers lists with their IP1
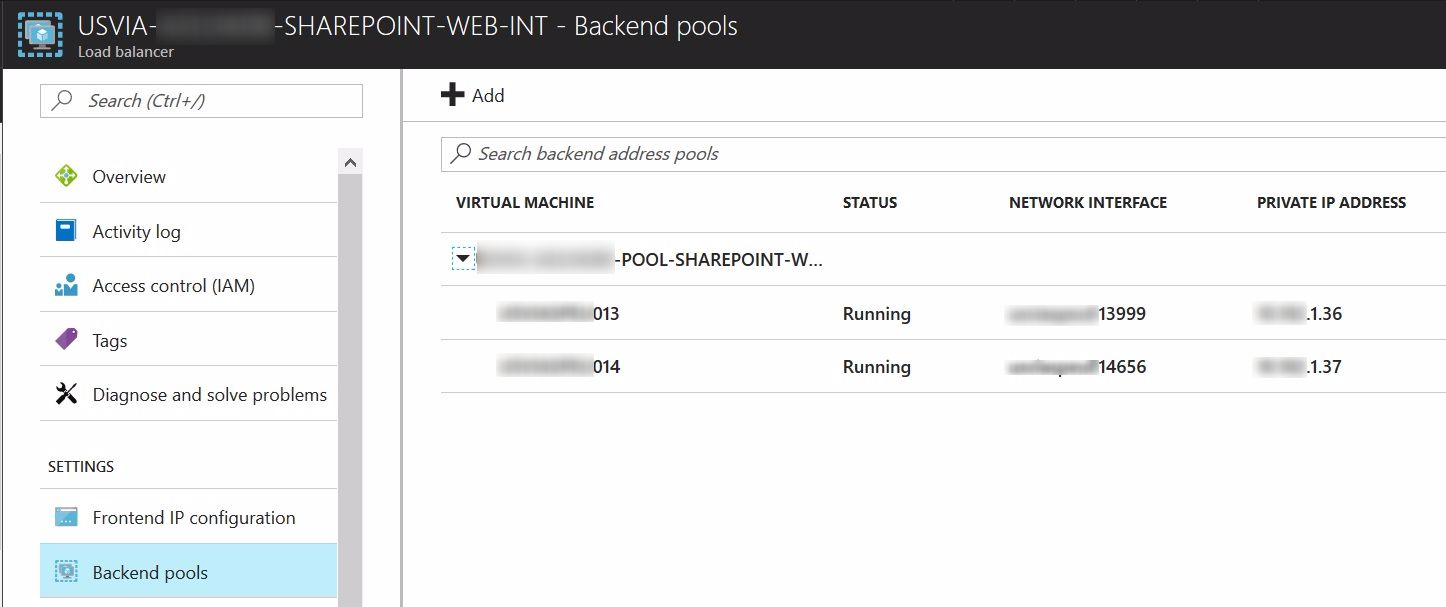
- Repeat the steps for Internal Load Balancer, but this time, add the VMs using their IP2
External Load Balancer:
Internal Load Balancer:
Step 3:
- Now, you can go ahead and configure your External load balancer rules
- Rule 1: port 443, backend port: 443 – so that all https requests remain on https
- Repeat this for Internal Load balancer
- This time Azure will accept the rules and your site will be accessible over https from over LAN and Internet both.
Step 4:
Now it’s time to look into how we can redirect users accessing the application over http to https.
We need to make use of Azure Load Balancer + URL Rewriting module of IIS to make this work.
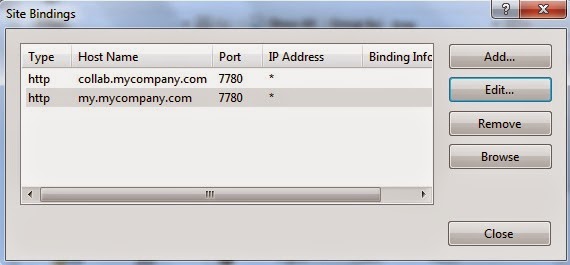
- Create an Empty Web Site in IIS on some random unused port, say 7780, with the same host headers as of your web application and map it to any folder.
- Allow port 7780 in Inbound Windows Firewall rule, if that’s enabled
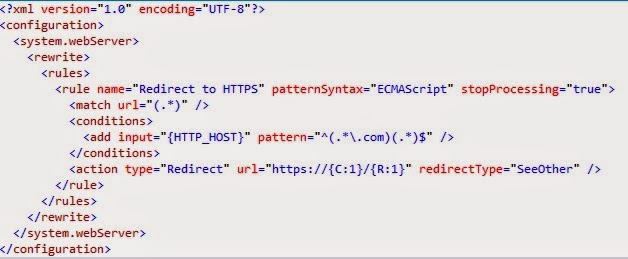
- Add a web.config file in the root folder of this new IIS web site with following content
- This config setting takes care of redirecting any incoming traffic on that IIS site to corresponding https url
Step 5:
- Now, how users will reach to this site – Add a rule in Azure External Load balancer with following settings
- Rule 2: port:80, backend port: 7780 – so that all http requests get redirected to IIS web site at port 7780.
- Add the same rule in Internal Load Balancer as well
- What essentially, it is doing is to accept users’ requests on http and redirect the traffic to IIS site hosted on port 7780 and since the IIS site on port 7780, is just doing a redirect, users will see their browser address bar getting changed to https 🙂
And we are done, now all your users accessing over Internet or company LAN, will always get redirected to https regardless of whether they are typing http or https.
Enjoy,
Anupam
2 comments
I’d just this minute thought of this idea to get around the poor implementation of http to https redirects in Application Gateway so thought I’d see if anyone else had done it.
I’m going to try your approach with that and see what happens.
Thanks!
I have this solution running to various customers, so I expect it to work for you as well… Enjoy…